
Getty Photographs
Hackers abused an antivirus service for 5 years to be able to infect finish customers with malware. The assault labored as a result of the service delivered updates over HTTP, a protocol weak to assaults that corrupt or tamper with knowledge because it travels over the Web.
The unknown hackers, who might have ties to the North Korean authorities, pulled off this feat by performing a man-in-the-middle (MiitM) assault that changed the real replace with a file that put in a complicated backdoor as a substitute, stated researchers from safety agency Avast as we speak.
eScan, an AV service headquartered in India, has delivered updates over HTTP since at the very least 2019, Avast researchers reported. This protocol offered a useful alternative for putting in the malware, which is tracked in safety circles below the identify GuptiMiner.
“This subtle operation has been performing MitM assaults concentrating on an replace mechanism of the eScan antivirus vendor,” Avast researchers Jan Rubín and Milánek wrote. “We disclosed the safety vulnerability to each eScan and the India CERT and acquired affirmation on 2023-07-31 from eScan that the problem was fastened and efficiently resolved.”
Advanced an infection chain
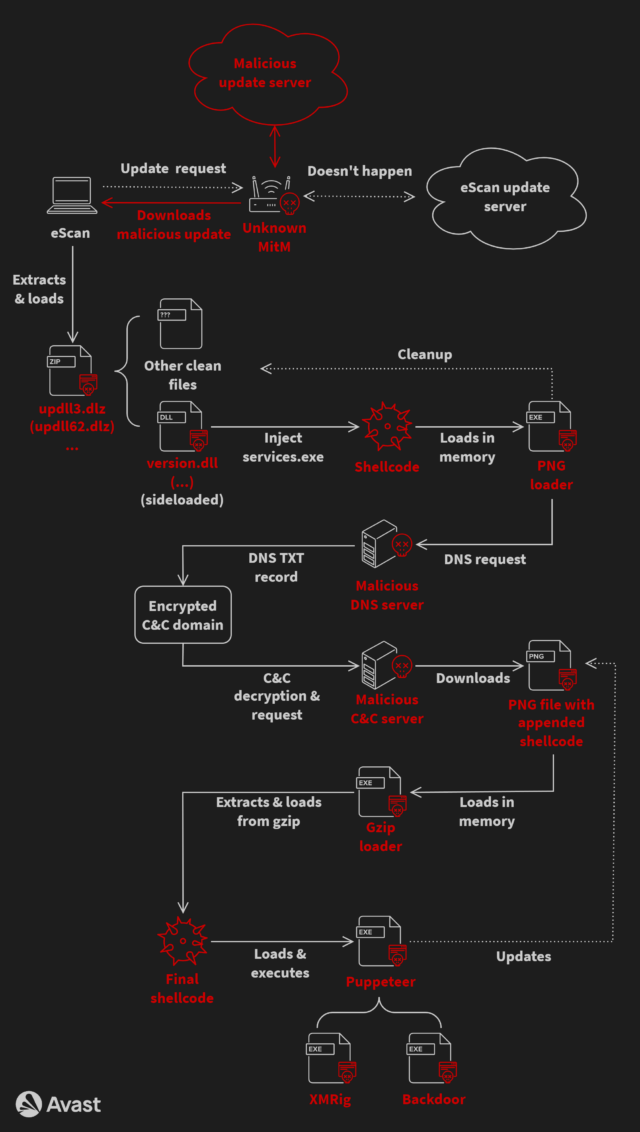
The complicated an infection chain began when eScan purposes checked in with the eScan replace system. The menace actors then carried out a MitM assault that allowed them to intercept the bundle despatched by the replace server and substitute it with a corrupted one which contained code to put in GuptiMiner. The Avast researchers nonetheless don’t know exactly how the attackers had been in a position to carry out the interception. They believe focused networks might have already got been compromised one way or the other to route visitors to a malicious middleman.
To decrease the probabilities of detection, the an infection file used DLL hijacking, a way that replaces authentic dynamic hyperlink library information utilized by most Microsoft apps with maliciously crafted ones that use the identical file identify. For added stealth, the an infection chain additionally relied on a customized area identify system (DNS) server that allowed it to make use of authentic domains when connecting to attacker-controlled channels.
Final yr, the attackers deserted the DNS approach and changed it with one other obfuscation approach generally known as IP handle masking. This concerned the next steps:
- Acquire an IP handle of a hardcoded server identify registered to the attacker by normal use of the gethostbyname API operate
- For that server, two IP addresses are returned—the primary is an IP handle which is a masked handle, and the second denotes an out there payload model and begins with 23.195. as its first two octets
- If the model is newer than the present one, the masked IP handle is de-masked, leading to an actual command-and-control (C&C) IP handle
- The true C&C IP handle is used together with a hardcoded fixed string (a part of a URL path) to obtain a file containing malicious shellcode
Some variants of the an infection chain stashed the malicious code inside a picture file to make them more durable to detect. The variants additionally put in a customized root TLS certificates that happy necessities by some focused methods that each one apps should be digitally signed earlier than being put in.
The payload contained a number of backdoors that had been activated when put in on giant networks. Curiously, the replace additionally delivered XMRig, an open-source bundle for mining cryptocurrency.
Avast
GuptiMiner has circulated since at the very least 2018 and has undergone a number of revisions. One searched compromised networks for methods operating Home windows 7 and Home windows Server 2008, presumably to ship exploits that labored on these earlier variations. One other supplied an interface for putting in special-purpose modules that might be custom-made for various victims. (This model additionally scanned the native system for saved personal keys and cryptocurrency wallets.)
The researchers had been shocked that malware that took such pains to fly below the radar would additionally set up a cryptocurrency miner, which by nature is often simple to detect. One risk is the attackers’ doable connection to Kimsuky, the monitoring identify for a gaggle backed by the North Korean authorities. Through the years, North Korea’s authorities has generated billions of {dollars} in cryptocurrency by means of malware put in on the gadgets of unwitting victims. The researchers made the doable connection after discovering similarities between a identified Kimsuky keylogger and code fragments used throughout the GuptiMiner operation.
The GuptiMiner assault is notable for exposing main shortcomings in eScan that went unnoticed for at the very least 5 years. Moreover not delivering updates over HTTPS, a medium not prone to MitM assaults, eScan additionally did not implement digital signing to make sure updates hadn’t been tampered with earlier than being put in. Representatives of eScan didn’t reply to an e mail asking why engineers designed the replace course of this fashion.
Individuals who use or have used eScan ought to examine the Avast publish for particulars on whether or not their methods are contaminated. It’s possible that almost all respected AV scanners can even detect this an infection.





